DigitalPersona U.are.U Personal fingerprint scanner
Review date: 17 July 2002. Last modified 03-Dec-2011.
Biometric authentication seems to be, on the face of it, a groovy idea. Do away with hard-to-remember passwords and easy-to-lose keys and cards; authenticate your identity with your voice, or your face, or your fingerprint. What could possibly be wrong with that?
Well, lots of things, actually.
High on the list is the fact that if biometric authentication is compromised - if someone finds a way to fake your voice or face or finger - you're up a brown and smelly creek without any way to propel your barbed wire canoe.
If someone rips off a password of yours, you can change it. If someone steals your credit card, you can cancel it. Lost a key? Change your locks.
But if someone figures out a way to duplicate your fingerprint or voiceprint or retinal or iris ID, there's nothing you can do. Well, OK, you can switch to a different finger or a different eye, but nature puts certain hard limits on how many times you can do that. Once you're out of organs, you're out of luck.
The limited number of biometrics each person carries around with them also makes it impossible to have a large number of different biometric keys. It's important to use different passwords, certificates, keys or what-have-you for different tasks; only things that don't really matter (like your New York Times login, for instance) should use the same password. Otherwise the guy that rips off the username and password list from the poorly secured e-store that sold you a T-shirt will also be able to access your bank accounts.
All this is only a problem, of course, if biometrics can be duplicated by normal human beings. The marketing departments at biometric ID companies have, historically, insisted that they can't. Sure, maybe the NSA can fake out a finger scanner, but some scungy little credit card fraudster isn't going to be able to manage it.
That's the story, anyway.
Thoughts like this were going through my head as I started playing with DigitalPersona's U.are.U Personal finger ID system.
DigitalPersona want two full stops in that product name, as well as the two capital letters. I'll meet them halfway and call it UareU from here on.
UareU Personal, in a nutshell, promises to deliver home and small office users of Windows 98, ME or XP from the pain of remembering passwords, and the insecurity of writing them down.
As finger scanners go, this isn't a terribly expensive one. Here in Australia, a single UareU Personal kit will set you back $AU231 including GST; they cost a bit less if you buy more. The US dealers listed on DigitalPersona's where-to-buy page list it for $US80 to $US100. The more expensive UareU Pro Workstation kit, for all Windows flavours from 95 to XP, has the same core functionality, plus networking and admin extras, and the ability to use passwords as well as fingerprints for access; UareU Personal is fingerprint-only.
There's also an Online version, specially made for remote Internet authentication. And software development kits, as well.
The UareU scanner itself is a solid little box about half the size of a cigarette packet. It's got a rubbery oval window on the top of it. It connects via USB.
Needless to say, I took it to bits before I even plugged it in. It's a tight-packed device, built around some rather trippy looking optics.
Using it
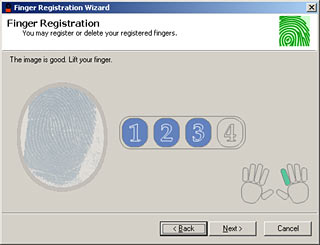
In Windows XP, UareU Personal was completely painless to set up and use. Install the software, restart, plug in the scanner, run the wizard to register a finger or three. Nothing to it.
The DigitalPersona site currently has "Under Construction" pages where the sensor and applications tech info should be, but the UareU scanner's optical sensor is obvious even to people who haven't taken it to bits. Most finger scanners use capacitive sensors.
The registration process is simple. Just put the relevant finger on the scanner when you're told, and if it gets four good images of it - which it probably will - then the finger's registered.
After that, you can use any registered finger to authenticate yourself from the WinXP Welcome screen, and you can also switch accounts - press your finger on the sensor while someone else is logged in, and you'll switch to your account.
When you put a registered finger on the scanner while someone's logged in...
![]()
...you'll get one of these two icons in the top left corner of the screen, depending on whether the system's recognised the finger or not.
If it recognises you, and you're already logged into your account...
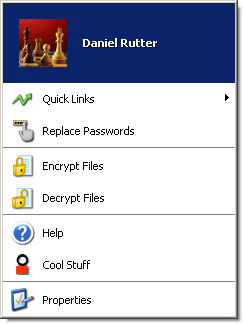
...this menu pops up.
Apart from letting you change the preferences settings for the UareU system, the menu also lets you set up "One Touch Internet" profiles, which allow you to log into password protected programs and Web sites with nothing but a fingerprint.
You can also encrypt and decrypt files, using... well, I'm not sure what sort of encryption it's using.
The DigitalPersona security page talks about 128 bit encryption being used to protect template and user data, which I presume includes files you choose to encrypt. It's also supposed to use 128 bit encryption on its USB data stream, to prevent wire-snooping attacks.
"128 bit encryption" doesn't tell you anything more than "V8 engine" does, mind you. There's a lot more you need to know about an encryption system before you can tell whether it's suitable for storing the plans for your time machine, assassination attempt or extra-marital affair.
Cracking a 128 bit encryption system with no weaknesses should take any currently plausible computer technology longer than the expected lifespan of the sun. Cracking "128 bit" encryption that has nasty known vulnerabilities, on the other hand, can take a desktop PC less time than it takes for the attacker to make a cup of coffee.
I'm perfectly happy to believe, however, that this system's encryption is as bulletproof as anybody using a product called "Personal" is ever likely to need.
I didn't bounce different people and different fingers off the UareU scanner for days on end, but I'm happy to say that it seems to have very good false rejection and false acceptance performance - very little of the former, none of the latter. If you're a real user, you're practically certain to be recognised, unless you put your finger on the scanner very sloppily indeed; you can even put your finger on the scanner sideways or upside down and it'll almost always be recognised. If not, just try again; it only takes a moment.
If your fingerprint isn't in the database - or if you're messing around with your nose, toes or other body parts - then you've got functionally no chance of being recognised as a real user.
That's great, and all, but it's not the problem. The problem is malicious attackers. Attackers aren't likely to try their own fingers on a scanner on the off-chance that their print happens to look enough like someone else's that it's accepted. That's about as sensible as stealing someone's ATM card, sticking it in a machine, and then trying random PINs.
Real attackers are going to try more intelligent strategies. Strategies which biometric security firms would apparently rather their customers not think about.
Faking it out
Tsutomu Matsumoto of Yokohama National University got the ball rolling in the cruelty-to-finger-scanners area with his study on the foolability of different scanners when presented with "fingers" made from silicone and gelatine.
You can read a PDF presentation which summarises Matsumoto's study here; the title page has the Starfleet logo on it, so it must be good. The full paper is here, and there's more on fake fingers here.
Matsumoto, in brief, fooled various sensors with fake fingers. Gelatine fingers worked better, because gelatine behaves, electrically, quite like real flesh; sensors that care about conductivity, which capacitive sensors do, aren't terribly likely to be faked out by a silicone finger.
The UareU scanner is optical and probably wouldn't know the difference, but I nonetheless decided to see if I could fool it with a gummi finger.
The easiest way to make a jelly fingertip (note to North Americans - here in the Commonwealth, what you call "jelly" is called "jam". What we call "jelly" is what you usually refer to using the Jell-O brand name) is by making a mould of a real finger, and then pouring hot strong gelatine solution into it. This isn't a very realistic attack, since it requires you to have a real user (or, at least, a real user's finger...) to make the mould, and they're not too likely to consent to that. You could perhaps trick them into it - latex hidden under a door handle, or something. But there's another way.
Tsutomu Matsumoto demonstrated that flat prints lifted from items the target has handled can be enhanced and etched onto circuit board material, and the etched board used to make a jelly finger, which will work pretty much as well as one made from a mould. This sort of jelly finger is flat, of course, but so is a real finger when you're pressing it onto a sensor plate.
Print-lifting and scanning and board-etching, I was not sufficiently enthusiastic to attempt. But I could just about manage the level of effort involved in making a moulded jelly finger-tip. So I did.
Matsumoto-san's mould-making material of choice is some sort of modelling plastic that may be available here in Australia, but don't ask me where.
I, therefore, tried a couple of other materials. Wax would be great, except that jelly fingers require a mould material that can tolerate having near-boiling gelatine solution poured into it. So I tried air-hardening clay. Useless. I then bought some epoxy putty. Which might be great. But I didn't try it, because I remembered that on my shelf I had a big (well, big-ish) bag of Dow Corning 3179 Dilatent Compound. Also known as plain old "coral" coloured Silly Putty.
One putty blob, plus a couple of packs of powdered gelatine from the supermarket, and I was in business.
This putty isn't actually Silly Putty branded dilatent compound, by the way; it's "Crazy Aaron's Thinking Putty". Which is the exact same thing, only it's sold at puttyworld.com. Which, by the way, also has a nice line of metallic-coloured bouncing putty, and provides adult-handful quantities of the stuff, rather than the kiddy-handful amounts you get in normal Silly Putty eggs.
You can buy "genuine" Silly Putty online from their store, including bulk packs, but they don't ship to Australia. Puttyworld do.
I was not being paid to tell you this when I first wrote this review. I'm now, I kid you not, in the Puttyworld affiliate program, so if you click here and then buy putty, I'll get a cut. But hey, it's good putty. Advertisement concludes.
Bouncing putty takes a finger imprint really well. And a quick experiment with some boiling water demonstrated that the stuff softens when it's hot, but not enough that the imprint loses significant detail.
You don't need a lot of putty to do this, by the way; an ordinary Silly Putty egg from a toy store would be perfectly adequate.
Aaaaanyway, it was now time to mix up the gelatine.
For ordinary jelly, you need only about one tablespoon of gelatine to every two cups of water - about a 7 to 200 weight-to-weight ratio. Twice that, if you like your jelly on the rubbery side.
For a fake fingertip, though, you need jelly as stiff as that in "gummi" lollies, which means something in the order of a one-to-one mix of water and gelatine, weight for weight.
Despite much enthusiastic stirring and double-boiler-immersing and microwave-ovening, I didn't manage to quite make it to 1:1 before my jelly started getting unacceptably lumpy. Drops of the stuff on a cold plate turned seriously rubbery, though, so I reckoned it'd be OK.
I'd put my putty in the fridge, and I pressed my thumb into it just before pouring the jelly in. Silly Putty always creeps towards a puddle-like state unless you've actually frozen it, so I wanted the minimum possible time between the impression and the moulding.
I poured on the gelatine solution, and into the freezer it went for a few minutes to set.
The jelly fingertip peeled off the putty very easily, as you'd expect - clean, cold Silly Putty doesn't stick very well to anything but itself. The gelatine was full of bubbles from my stirring, but the jelly thumb nonetheless had a pretty good complement of print-ridges on it...
...as you can see in this picture, where it's backlit by an LED flashlight.
Ugly and bubble-y the jelly thumb was, but the UareU scanner loved it. It thought the jelly finger was a real one more than 50% of the time. And since you can attempt recognition about once a second, that means it'd be trivially easy to log in with a thing like this, even with people watching. Trim the jelly so it fits over the end of your real finger, and some very rudimentary prestidigitation will keep your fakery from the attention of onlookers.
I also found it was possible to enrol the jelly thumb as a new finger. It took me four attempts to do it, and its recognition rate wasn't any better than when I was trying to match it to my real finger. But that's still quite good enough to be useable in an, um, covert situation.
Overall
The UareU scanner's vulnerabilities are not an isolated problem. Commercial biometric authentication systems, so far, all seem to be pretty flaky, by themselves.
Earlier this year, German tech mag c't tested nine fingerprint scanners (six capacitive, two optical and one thermal), plus Panasonic's Authenticam iris scanner, and Cognitec Systems' FaceVACS-Logon facial recognition system. All of the widgets tested were current models, and all came with impressive marketing claims.
And all of them, in layman's terms, sucked, if used as the only source of identification.
Two finger scanners c't tested just didn't work properly. Of the remainder, the capacitive sensors could be fooled in a number of ways if an authorised user hasn't cleaned the sensor after fingering it. A latent print on many capacitive sensors can be revived by, for instance, breathing on it, applying graphite powder, or pressing a plastic carrier bag with water in it up against the sensor.
The graphite powder method works with lifted prints, too - follow your target to the pub, grab his glass after he's finished with it, dust a print with graphite, lift it with tape, and you're ready to go.
Optical sensors didn't fare any better. C't fooled them with silicone fingers made from an impression in wax, and also succeeded with backlit graphite print-copies on tape.
Few of these methods would attract attention if you did them in a normal office; you could get away with any of them if you were hiding in someone's cubicle. Anyone with half-decent knowledge of close-up magic would probably be able to pull most of them off even with a security guard watching. James Randi could probably steal the guard's gun, while he was at it.
The thermal-sensor finger scanner scored better. It was only somewhat susceptible to silicone-finger fooling, and not at all susceptible to other techniques. I'd be interested to see how a gelatine finger goes on a thermal sensor; it seems likely to behave, thermally, quite like the real thing.
In case you're wondering and don't have time to read the c't piece, the iris scanner was defeatable with a picture of an enrolled user's eye with a hole in the middle through which the attacker's pupil was visible, and the facial recognition rig would perfectly happily recognise still images and video clips of users that were shown to it on a laptop's screen.
All this doesn't mean that biometric systems are A Bad Thing. Only important systems that depend on nothing but biometrics are.
If all your office PC needs to identify you is a thumbprint, then someone in the office who hates you and fakes out the sensor can send highly creative e-mail in your name to all sorts of entertainingly important people. That's bad.
But if an account-tracking finger scanner's installed on the snack machine to save people from having to feed it change, the worst anybody can do to you is buy stuff on your tab. Which is likely to look just a weeny bit suspicious, if they buy enough to do you real financial harm.
The UareU Personal system is fingerprint-only. You can't have a print and a password. Of course, Joe Home User doesn't want to still have to use passwords; the big deal about UareU Personal is that it liberates you from remembering the darn things.
But that makes this a nothing-but-biometrics system, which means you shouldn't use it for anything important, if you think there's any chance that someone a bit creative (offspring, siblings and spouses included) may be able to get physical access to your prints, and to your PC.
Any Security Dude (check to make sure that's what his business card says) will tell you that authentication's based around what you are, what you have, and what you know. Any system based on only one of these things - like UareU Personal - will be insecure. That's why people use alarm systems as well as house keys - the keys are something you have, the alarm code is something you know. The same applies to ATM cards and PINs. People are thinking about this stuff.
The biometric-only problem is just a limitation of the UareU Personal package, though. The somewhat more expensive UareU Pro Workstation package ($AU324.50 including GST) has the same finger scanner, but its software supports fingerprint-plus-password authentication. That makes it no use for password-haters, of course, but it should provide genuinely superior security. Well, as long as your passwords aren't written on a Post-It note stuck on your monitor, or hidden in one of the other places where password-hunters always look, like the underside of your desk.
Getting back to UareU Personal, though - does it stop you from having to remember passwords? Yes.
Does this enhance your system security? Yes, if you've got the usual computer user's attitude to password choice and secrecy, which is that these aren't things you need to worry about.
Is UareU Personal truly secure, though, in a trust-it-with-your-life-savings way?
Nope. And neither's any other biometric-only system, to date.
U.are.U Personal kindly provided by Automa.